In the rapidly evolving landscape of cybersecurity, safeguarding web assets is of utmost importance for businesses and users alike. As cyber threats continue to grow in complexity, web developers and administrators must explore innovative ways to fortify the security of their websites and web applications. One effective and widely adopted technique to bolster web security is the implementation of HTTP security headers.
These additional instructions, sent by web servers along with HTTP responses, play a crucial role in preventing various types of web vulnerabilities and attacks. In this article, we will delve into the significance of HTTP security headers, understand their role in mitigating common risks, and explore some commonly used security headers to create a safer online browsing experience.
What Are HTTP Security Headers?
HTTP Security Headers | Part 01
HTTP security headers are additional instructions sent by a web server along with HTTP responses to a user's browser. These headers play a crucial role in enhancing the security of websites and web applications by providing specific guidance to the browser on how tohandle the contentand behave when interacting with the website.
The primary purpose of HTTP security headers is to prevent various types of web vulnerabilities and attacks. By configuring and deploying these headers, web developers can mitigate a wide range of security risks, including but not limited to:
- Cross-Site Scripting (XSS) -XSS attacks involve injecting malicious scripts into web pages viewed by other users, potentially leading to data theft or manipulation.
- Clickjacking - Clickjacking attacks trick users into clicking on elements of a web page that are hidden or disguised, leading them to perform unintended actions.
- Content Sniffing -Content sniffing, also known as MIME sniffing, is when a browser attempts to interpret a file's content type based on its content rather than the declared MIME type, potentially leading to security vulnerabilities.
- Code Injection -Code injection attacks involve inserting malicious code into a web application, leading to unauthorized access or data manipulation.
- Man-in-the-Middle Attacks (MITM) -MITM attacks involve intercepting communication between a user's browser and the webserver to eavesdrop, modify, or steal sensitive information.
Importance Of HTTP Security Headers In Web Security
HTTP security headers play a crucial role in enhancing web security by providing an additional layer of protection against various types of web vulnerabilities and attacks. As cyber threats continue to evolve and become more sophisticated, implementing these headers has become a standard practice for web developers and administrators. The importance of HTTP security headers in web security can be understood through the following key points:
- Mitigation of Common Web Vulnerabilities -HTTP security headers help prevent common web vulnerabilities such as cross-site scripting (XSS), clickjacking, content sniffing, and code injection attacks. By configuring these headers, web developers can significantly reduce the risk of exploitation and unauthorized access to sensitive data.
- Protection of User Data and Privacy -Websites often handle sensitive user information, such as personal data and login credentials. HTTP security headers, such as Strict-Transport-Security (HSTS), enforce secure communication through HTTPS, ensuring that data transmitted between the user's browser and the server remains encrypted and protected from eavesdropping and interception.
- Enforcement of Secure Communication Protocols -Security headers like HSTS ensure that the website is accessed only over HTTPS, reducing the chances of man-in-the-middle (MITM) attacks that attempt to downgrade the connection to unencrypted HTTP.
- Preventing Clickjacking Attacks -X-Frame-Options header guards against clickjacking attacks by preventing a website from being embedded within an iframe on malicious sites. This prevents users from unknowingly performing actions on the hidden website while interacting with the visible malicious content.
- Controlling Content Loading -Content-Security-Policy (CSP) enables administrators to specify which content sources are trusted and allowed to be executed on their websites. This granular control helps mitigate XSS attacks and restricts the loading of potentially harmful resources.
- Preventing Content Sniffing -X-Content-Type-Options header prevents browsers from attempting to "sniff" the content type, reducing the risk of executing files with incorrect MIME types that could lead to security vulnerabilities.
- Enhancing User Trust and Experience -Implementing robust security measures through HTTP security headers inspires confidence in website visitors. Users are more likely to trust a site that prioritizes security, leading to increased engagement and positive user experiences.
- Positive Impact on SEORankings -Search engines, such as Google, consider website security as a ranking factor. Websites that prioritize security by implementing HTTPS and various security headers are often rewarded with better search enginerankings, improving their visibility and organic traffic.
- Staying Compliant with Industry Standards -Many industries and regulatory frameworks require websites to implement specific security measures to protect user data. HTTP security headers can help websites meet these compliance requirements.
Strict-Transport-Security (HSTS)

What is HSTS (HTTP Strict Transport Security)? HSTS explained simply.
Strict-Transport-Security (HSTS) is an HTTP security header that instructs the user's browser to interact with a website only via HTTPS (HyperText Transfer Protocol Secure). When a website sends the HSTS header in its server response, it informs the browser to remember and enforce this policy for a specified duration, ensuring that all future requests to the same website are made over a secure HTTPS connection.
The primary purpose of HSTS is to prevent potential downgrade attacks, such as SSL-stripping or protocol downgrade attacks, where an attacker attempts to intercept the initial HTTP request and downgrade it to an insecure HTTP connection. By enforcing HTTPS for all communications, HSTS mitigates the risk of man-in-the-middle attacks (MITM) and ensures that user data, login credentials, and sensitive information remain encrypted and protected from eavesdropping or interception.
Once the user's browser receives the HSTS header from the website, it will automatically convert any insecure HTTP request to HTTPS, even if the user manually enters an HTTP URL. This behavior ensures a seamless and secure browsing experience for users, reducing the chances of accidentally accessing a website over an unencrypted connection.
To implement HSTS on a website, the server response should include the following header:
Strict-Transport-Security: max-age=31536000; includeSubDomains
In this example, max-age=31536000indicates that the HSTS policy should be cached and enforced by the browser for one year (31536000 seconds). The includeSubDomainsdirective extends the HSTS policy to cover all subdomains of the website, making it even more secure.
Content-Security-Policy (CSP)
Content Security Policy (CSP) Explained
Content-Security-Policy (CSP) is an important HTTP security header that allows website administrators to specify which content sources are trusted and permitted to be loaded by the user's browser. By controlling the origins from which scripts, styles, images, fonts, and other resources can be executed or loaded, CSP helps mitigate the risk of various web-based attacks, especially cross-site scripting (XSS) vulnerabilities.
The primary objective of CSP is to prevent malicious code injection, unauthorized data exfiltration, and other types of code execution attacks that can occur if a website's content is compromised. By defining a whitelist of trusted sources, CSP instructs the browser to only load resources from those approved origins, blocking any attempts to execute scripts or load content from unauthorized or potentially dangerous locations. Implementing CSP on a website provides the following security benefits:
- Mitigation of XSS Attacks -XSS attacks involve injecting malicious scripts into a web page, which can be used to steal sensitive information or perform unauthorized actions on behalf of the user. CSP helps prevent XSS by blocking the execution of scripts from untrusted sources.
- Protection Against Data Injection - By restricting content loading to specified domains, CSP mitigates the risk of data injection attacks where an attacker attempts to inject malicious data into a website, potentially altering the site's behavior or leaking sensitive information.
- Preventing Clickjacking -CSP can also guard against clickjacking attacks by controlling which domains are allowed to frame the website. This prevents the site from being embedded in hidden iframes on malicious websites, reducing the risk of users unintentionally interacting with harmful content.
To apply CSP to a website, the server's response should include the Content-Security-Policy header with a set of directives defining the trusted sources. The configuration can be as permissive or restrictive as necessary, depending on the specific requirements and resources used by the website. Example CSP header:
Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline'; style-src 'self' 'unsafe-inline'; img-src 'self' data:; font-src 'self';
In this example, the CSP policy allows scripts and styles to be loaded from the same domain ('self') and allows inline scripts and styles using 'unsafe-inline'. Additionally, it allows images from the same domain and data URLs, as well as fonts from the same domain.
X-XSS-Protection

The Most Important X-XSS Protection header and Security Best practices
X-XSS-Protection is an HTTP security header designed to enable or disable the browser's built-in cross-site scripting (XSS) protection mechanism. XSS attacks involve injecting malicious scripts into web pages viewed by other users, potentially leading to data theft, unauthorized actions, or manipulation of website content. The X-XSS-Protection header helps mitigate these attacks by instructing the browser on how to handle suspected XSS attempts. The header can have three possible values:
- X-XSS-Protection: 0- Disables the XSS protection mechanism in the browser.
- X-XSS-Protection: 1- Enables the XSS protection mechanism and attempts to sanitize or block the suspicious script. If a suspected XSS attack is detected, the browser will prevent the page from loading or rendering the script.
- X-XSS-Protection: 1; mode=block- Similar to the value of 1, this option also enables the XSS protection mechanism. However, if an XSS attack is detected, the browser will not attempt to sanitize the script but will block the entire page from loading, effectively preventing any XSS execution.
Example usage of X-XSS-Protection header:
X-XSS-Protection: 1; mode=block
By setting the X-XSS-Protection header with the value of 1 or 1; mode=block, website administrators can ensure that modern browsers will actively protect users against potential XSS attacks. This additional security layer complements other security measures, such as Content-Security-Policy (CSP), to strengthen the overall defense against XSS vulnerabilities.
However, it's essential to note that the X-XSS-Protection header is not universally supported by all modern browsers, and its effectiveness may vary depending on the browser version. As a best practice, it is recommended to implement other security measures, such as input validation and output encoding, in conjunction with the X-XSS-Protection header for comprehensive protection against XSS attacks.
X-Content-Type-Options

What is the X-Content-Type-Options Header?
X-Content-Type-Options is an HTTP security header that helps prevent content sniffing or MIME sniffing attacks in modern web browsers. Content sniffing occurs when a browser attempts to interpret the MIME type of a resource based on its content, instead of relying on the MIME type specified by the server. This behavior can lead to security vulnerabilities if the browser misinterprets the resource type and processes it in an unexpected and potentially harmful way.
The X-Content-Type-Options header can have one of two values:
- X-Content-Type-Options: nosniff- This value instructs the browser not to perform content sniffing and to strictly adhere to the declared MIME type provided by the server.
- X-Content-Type-Options: no-sniff- This alternative value serves the same purpose as "nosniff" and is supported by some older browsers.
Example usage of X-Content-Type-Options header:
X-Content-Type-Options: nosniff
By including the X-Content-Type-Options header in the server response, web developers can mitigate the risks associated with content sniffing attacks. For example, it helps protect against attackers attempting to disguise malicious scripts or executable content with misleading MIME types to trick browsers into executing them.
When the X-Content-Type-Options header is set to "nosniff," modern browsers will honor the declared MIME type without attempting to perform content sniffing. This ensures that resources are handled according to their intended content type, reducing the potential for security exploits and unexpected behavior.
While X-Content-Type-Options is a valuable security header, it is important to complement it with other security measures, such as input validation and output encoding, to create a robust defense against a variety of web vulnerabilities.
X-Frame-Options
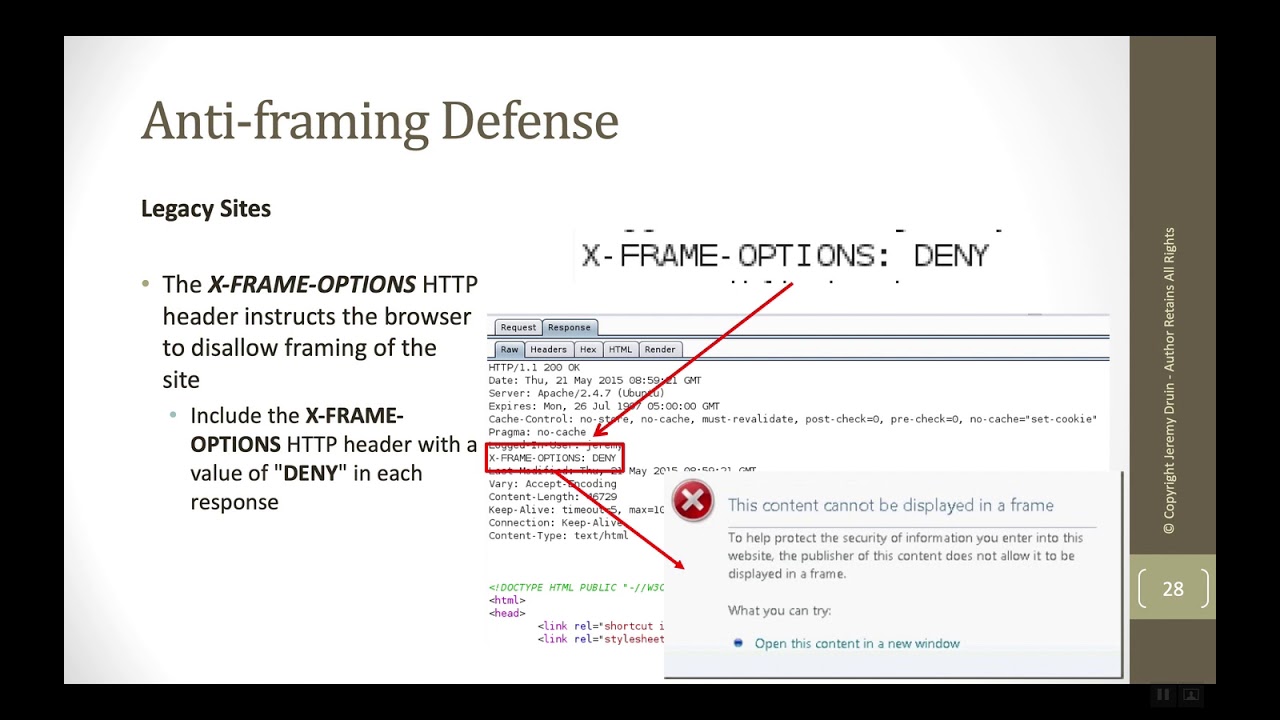
What is the X-Frame-Options Header?
X-Frame-Options is an HTTP security header that provides a defense against clickjacking attacks, also known as UI (User Interface) redressing or UI rewriting attacks. Clickjacking involves tricking users into clicking on elements of a web page that are hidden or disguised, which can lead to unintended actions being performed without the user's knowledge or consent. These attacks are typically executed by overlaying the original website with a maliciously crafted transparent iframe or by framing the website within a malicious page.
The X-Frame-Options header allows website administrators to control whether their website can be embedded in an iframe on another site. It provides three possible values:
- X-Frame-Options: DENY- This value indicates that the website should not be embedded in any iframe, and attempting to do so will be denied by the browser.
- X-Frame-Options: SAMEORIGIN- This value allows the website to be embedded only in iframes that originate from the same domain as the website itself. Requests from other domains will be denied.
- X-Frame-Options: ALLOW-FROM uri- This value permits the website to be embedded in iframes from a specific URI or domain. Allowing specific sources requires specifying the exact URI or domain in place of "uri."
Example usage of X-Frame-Options header:
X-Frame-Options: DENY
By setting the X-Frame-Options header with the value of "DENY," website administrators can effectively protect their websites from being framed or embedded within iframes on other websites. This helps prevent clickjacking attacks, as the browser will refuse to display the website within any iframe, ensuring that the content is viewed only in its intended context.
It's important to note that while X-Frame-Options is a useful security header, it is supported by modern browsers. In some cases, newer standards such as the Content-Security-Policy (CSP) frame-ancestors directive are recommended for providing more robust control over framing permissions.
Web developers should carefully consider their website's requirements and compatibility with different browsers when choosing the appropriate framing protection mechanism. Regular testing and validation are essential to ensure that the X-Frame-Options header does not adversely impact legitimate functionalities or user experienceon the website.
Referrer-Policy

What is Referrer-Policy HTTP Header?
Referrer-Policy is an HTTP security header that allows website administrators to control the amount of information included in the Refererheader when navigating to external sites. The Refererheader is automatically sent by the user's browser and contains the URL of the page from which the request originated. By configuring the Referrer-Policy header, web developers can enhance user privacy and control how much information is shared with external links.
The Referrer-Policy header can have several values, each representing a different level of information sharing:
- Referrer-Policy: no-referrer- This value indicates that no referrer information will be sent in the Refererheader. When users click on links to external sites, the Refererheader will not be included, thus preserving their privacy. This is the most privacy-conscious setting.
- Referrer-Policy: no-referrer-when-downgrade- This is the default value. It means that the Refererheader will be included when navigating from HTTPS to HTTP URLs, but it will be omitted when moving from HTTPS to HTTPS or from HTTP to HTTP.
- Referrer-Policy: origin- This value sends only the origin part of the referring URL (scheme, host, and port), excluding any path or query parameters.
- Referrer-Policy: origin-when-cross-origin- This value sends the full Refererheader when navigating to the same origin (same domain), but only sends the origin part when the destination is a different origin (cross-origin).
- Referrer-Policy: same-origin- The Refererheader is included only when navigating within the same origin (same domain).
- Referrer-Policy: strict-origin- This value sends the full Refererheader when navigating within the same site and between subdomains of the same site. However, it omits the Refererheader when navigating to a different origin.
- Referrer-Policy: strict-origin-when-cross-origin- This is a combination of "strict-origin" and "origin-when-cross-origin" values. It sends the full Refererheader within the same site and between subdomains, but only the origin part when the destination is a different origin.
Example usage of Referrer-Policy header:
Referrer-Policy: strict-origin-when-cross-origin
By setting the Referrer-Policy header appropriately, website administrators can control the level of referrer information shared with external links, thus improving user privacy and security.
How To Implement HTTP Security Headers?

How To Implement HTTP Security Headers in your Website or Webserver
Implementing HTTP security headers involves configuring your web server to include the appropriate security headers in its HTTP responses. The exact implementation process can vary depending on the web server software you are using (e.g., Apache, Nginx, IIS) and your website's specific needs. Below, I'll provide a general guide to implementing HTTP security headers:
- Identify Necessary Headers - Determine which security headers are suitable for your website's security needs. The most common headers include Strict-Transport-Security (HSTS), Content-Security-Policy (CSP), X-XSS-Protection, X-Content-Type-Options, X-Frame-Options, and Referrer-Policy.
- Modify Server Configuration -Access your web server's configuration file or virtual host settings. The exact location and method for modifying the configuration file vary based on the web server software.
- Enable Headers with Appropriate Values -For each security header you want to enable, add the corresponding header line with its value to your server's configuration. Below are some examples:
Enabling HSTS for one year with subdomain coverage - Strict-Transport-Security: max-age=31536000; includeSubDomains
Implementing a basic CSP policy - Content-Security-Policy: default-src 'self';
Enabling XSS protection in the browser - X-XSS-Protection: 1; mode=block
Preventing content sniffing - X-Content-Type-Options: nosniff
Guarding against clickjacking - X-Frame-Options: DENY
Setting Referrer-Policy to limit referrer information - Referrer-Policy: strict-origin-when-cross-origin
- Verify Configuration:After modifying the server configuration, verify that the headers are included correctly in the HTTP responses. You can use browser developer tools or online security header-checking tools to inspect the server's responses and ensure the headers are present.
- Test and Debug:Thoroughly test the website to ensure that the implemented security headers do not break any functionalities or interfere with user experience. Make any necessary adjustments or debugging as needed.
- Periodic Review and Updates:Security threats and best practices evolve over time, so it's essential to periodically review and update the security headers. Stay informed about changes in security standards and adjust the headers accordingly to maintain an optimal security posture.
People Also Ask
How Do HTTP Security Headers Work?
HTTP security headers work by providing specific instructions to the user's browser on how to handle the content and behave when interacting with the website. They help prevent security risks such as cross-site scripting (XSS), clickjacking, content sniffing, and more.
How Do I Enable HTTP Security Headers On Apache Web Server?
To enable HTTP security headers on an Apache web server, you can use the Headerdirective in the server configuration file. For example, to enable HSTS, add Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"to the configuration.
Are HTTP Security Headers Supported By All Browsers?
While most modern browsers support HTTP security headers, some older browsers may not fully support certain headers. It's crucial to test your website's compatibility across different browsers to ensure consistent security measures.
How Often Should I Review And Update HTTP Security Headers?
It is recommended to review and update HTTP security headers periodically, especially when there are changes in your website's structure, and functionality, or the emergence of new security threats. Regular reviews help ensure that your headers remain effective and up-to-date.
Conclusion
In the battle against cyber threats, HTTP security headers stand as formidable defenders of web assets. These additional instructions, thoughtfully integrated into HTTP responses, empower web developers and administrators to reinforce their websites' security posture. As the web continues to evolve, staying vigilant about implementing and updating these security headers will remain paramount in protecting users and ensuring the integrity of web assets in an ever-changing digital landscape.